Is your business well protected against errors and fraud? Check it out using the 10 essential steps of internal control.
The internal control system is a central element in reducing the risk of error or fraud. However, it is not always easy for a company to find its way around recommendations such as those of COSO (Committee Of Sponsoring Organizations of the Treadway Commission).
In the 10 steps below, discover the tips learned in the field over the last 15 years.

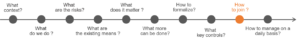
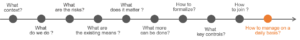
1- Definition of the scope of internal control
Firstly, the scope of action of internal control must be defined. This is certainly the most important step, the one that will give internal control its backbone. Three plans provide a clear and comprehensive starting framework:
- The geographical framework, which enables to formalize the locations that will be included in internal control.
- The activities or processes concerned.
- The families of risks (called “objectives” in COSO) that internal control will help to better control.
Therefore, three essential questions must be asked to define this scope of action:
- Which sites and subsidiaries are concerned?
- Which activities (processes) are concerned?
- What are the families of risks that internal control will help reduce?
The families of risks can be as follows:
- Financial: risks that could cause the company to lose money.
- Financial statement (or reporting): risks of anomalies in the accounts, incorrect accounting information, etc.
- Compliance: risks that could put the company in a situation where it does not comply with standards or laws.
- Operational: risks that may prevent the company from fulfilling its mission
- Personal health: risks that may affect the physical or psychological health of people connected with the company.
- Information security: risks affecting the confidentiality, integrity and accessibility of information
- Image: risks that can affect the company’s reputation
- Environment: risks that may affect the environment (air, water, soil, space, raw materials, energy, etc.).
Since internal control comes from the accounting field, it often covers at least the risks related to the financial statements (reporting).
2- Identification of the activities carried out
Then, once the scope of action has been defined, it is necessary to list the activities (or processes) carried out by the company in order to identify, in a second step, the risks associated with each process. The idea is to simply answer the question “What do we do in the company? ».
Activities vary from one company to another and it is essential to highlight the activities specific to each establishment.
In other words, the level of detail in identifying activities must be appropriate and consistent across sectors. For example, the following three sentences relate to the same process but do not provide the same levels of information:
- “I do accounting”
- “I pay supplier invoices”
- “I am entering accounting data”
This is why it is necessary to define the right environment to identify the activities that are carried out, without falling into a list of micro-tasks.
3- Identification of risks
The risks to which the company is exposed mainly result from the activities carried out. In this step, the question must therefore be asked for each activity: “What are the risks related to the families of risks selected? ». For example, for the “Payment of supplier invoices” process, what are the financial, operational or financial reporting risks ?
The identification of risks can result in an immeasurable inventory of possible risks. Even if many risks can be envisaged, care must be taken to remain close to reality. One solution is to start with situations already experienced by the company or in its sector of activity. For example, if your company has already made mistakes in salaries, you know that there is this risk that you will have to protect yourself against.
4- Identification of existing controls
In the context of internal control, the word “control” covers all the measures used to control a risk: control action, procedure, regulations, control software, tangible protection measures, etc.
Based on its past experience and knowledge of its business sector, each company already has internal controls and effective procedures to control certain risks. It is important to identify them. Often, 90% of controls already exist but are not formalized.
In front of each risk, it is therefore sufficient to identify the mitigation measures.
In addition, “controls of controls” (or surveillance of controls) should be added here if they already exist. For example: quarterly verification of the realization of the “monthly salary control”.
5- Risk assessment
Not all risks are the same and not all companies are equally exposed to risk. It is then a question of assessing the risks, in relation to the reality of the company, to define whether the mitigation measures are sufficient and whether controls need to be added.
Even if this step is not mandatory and may seem time-consuming, establishing “criticality” makes it possible to sort risks according to their importance. This “criticality” takes into account the likelihood of a risk occurring and the impact if it does occur.
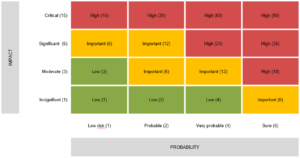
For example, when editing payslips, errors are very likely, yet the impact of this risk on the survival of the company is rather moderate. Conversely, the risk of fraud for a banking institution would have a critical impact, but also has a high probability if no control measures are put in place. The risk will therefore be serious, with a maximum score of 90, indicating a top priority.
6- Risk management

There are four possible strategies for dealing with risk when implementing internal control: avoid risk, reduce risk, transfer or share risk, and accept risk.
Take the example collecting of invoices in cash. When collecting invoices, human or software errors are always possible, or even highly probable. There are therefore risks associated with this activity. Here are four possible strategies to deal with these risks:
- Avoid: Stop collecting cash invoices. There will be no more cash in the company. This will avoid (eliminate) the “Risk of cash register error” or the “Risk of cash being stolen from the register”.
- Reduce: Setting up a control on the collection of invoices with a step of checking the amount in the cash register will reduce the risk.
- Transfer or share: Take out specific insurance for theft, this amounts to transferring or sharing the risk.
- Accept: Do not make it a priority and accept that sometimes there will be errors in the collection of invoices and that the consequences will have to be dealt with a case-by-case basis, this amounts to accepting the risk.
If the existing controls are not sufficient according to the company’s “risk appetite”, additional controls must be put in place and “risk mitigation projects” must be initiated.
7- Description of the mitigation measures
It is not a question of creating mountains of documents that will be forgotten on a shelf, but rather of making a selection. The objective is to identify the mitigation measures that need to be documented in order to reduce the risks.
Thus, it is a question of describing control actions, processes, procedures, regulations, etc.
For example, when several departments work together, it is relevant to describe the cross-functional process to improve cooperation between departments and reduce risks due to poor coordination.
Documenting a mitigation measure should enable to:
- Reduce errors
- Clarify the responsibilities of employees
- Guarantee that controls are always carried out in a homogeneous manner
- Ensure the continuity of the activity in case of absence of a collaborator
The documentation must be adapted. It can be a simple checklist to a full set of rules, or an explanatory video. The important thing is to find the right form that will add value through its clarity.
8- Identification of key controls and description of surveillance
It is essential to decide which controls are worth checking. This monitoring ensures that controls are “done and done right”.
For example, if you have set up a monthly control to check computer access, it may be a wise to create a surveillance on this point. This may involve the establishment an annual control to validate that the “computer access control” is being done properly. This is to minimize information security risks.
Too many controls kill control! Avoid defining too many key controls, as you will then have to invest precious time in implementing them.
9- Communication and training of employees to implement internal control
Internal control will only become a reality and an effective risk management tool when employees see its usefulness. Don’t neglect the communication and training required to ensure that everyone adheres to it.
While it is important to demonstrate the usefulness of internal control in relation to legal obligations, it is especially important to demonstrate to employees that internal control will bring them peace of mind, fewer errors and fewer omissions. They will be reassured to work in an environment where risks are controlled.
10- Management of internal control over time
Finally, even if your internal control system is effective at this stage, it is important to understand that it will live and evolve with the company. It is not ah ad-hoc and isolated act that is dealt with once and for all.
In order for it to be always useful and effective, it is necessary to :
- Reassess the risks once a year
- Ensure compliance with new legislation
- Maintain up-to-date documentation
- Monitor the proper implementation of controls and monitoring
- Monitor risk mitigation projects
- Tracking incidents that occur and treating them as a source of improvement
Obviously, changes and adjustments must be reflected in updated documentation and supported by clear and effective communication. Using internal control software can greatly simplify the description and management of your system.
In short, these 10 steps structure the implementation of internal control and its follow-up. They will enable you to take full advantage of an effective internal control adapted to your company to the satisfaction of your employees and management.
