Would you like to implement an Information Security Management System (ISMS) or obtain ISO 27001 certification?
Good news! Optimiso Group reveals its best practices, successfully applied by our customers over the last 15 years.
These 16 steps will provide you with a turnkey project for implementing your ISO 27001-certified ISMS.

1/ Presenting the project to employees
As with any project management, communication with employees is essential to ensure its success. Ideally, this presentation should be made face-to-face, by videoconference or in writing. The most important thing is to present the following points:
- The purpose of ISO 27001 certification
- What ISO 27001 is
- Benefits for employees and the company
- Project stages and deadlines
- Individual involvement
- Management support
2/ Description of the context and scope of ISO 27001 certification
The ISO 27001 standard requires you to define your company’s context, i.e. the environment in which it operates. To do this, you’ll need to define :
- External issues: for this, you can use the PESTEL model: Political, Economic, Societal, Ecological, Technological and Legal.
- Internal issues: corporate culture, values, etc.
- Interested parties: customers, unions, pressure groups, private or public shareholders, authorities, etc.
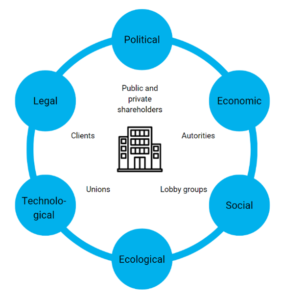
The first step is to define the scope of ISO 27001 certification. Let’s take the example of a company like Optimiso Group, which develops software and provides consulting services. Should only the development department be certified, or all the company’s activities? This step will provide a framework for all the actions required to ensure compliance with ISO 27001.
3/ Inventory of information assets
An information asset is an important resource linked to information. It can be data, computer systems, databases, confidential information or any other element of value to an organization. It is important not to confuse them with accounting assets.
In this stage, therefore, we need to identify all the assets owned by the company, as well as the related media.
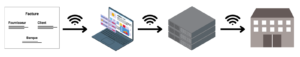
In this corporate accounting example, we find several information assets :
- An invoice, containing information such as supplier, products, prices, bank details, etc.
- Accounting software to manage all the company’s invoices
- A server that hosts the accounting software on a SaaS basis
- A network through which all information transits
- A datacenter to host the servers
Now that all your information assets have been identified, it’s time to manage and sort them according to their importance, to prioritize future actions.
4/ Information security policy
In this 4th stage of the ISO 27001 certification project, we need to draw up a policy formalizing the following elements:
- Management commitment
- Company purpose
- Commitment to information security
- Commitment to continuous improvement
This policy can be added to the other policies often found in companies (e.g. quality or environmental policies). It is important that this policy is communicated and understood by employees and interested parties.
5/ Defining roles and responsibilities
As part of ISO 27001 certification, you need to know who does what. You will need to define the various roles and responsibilities:
- Information security manager
- Information security committee members
- IT managers
- Asset managers
- Backup manager
- Controls manager
6/ Risk analysis
This stage involves identifying and assessing risks. Prior to this, it is important to have a policy defining the criteria for risk assessment. In this assessment, it is important to take into account the three impacts linked to information security: Confidentiality, Integrity and Accessibility.
Let’s take an example from the medical field, with patient medical information as an information asset.
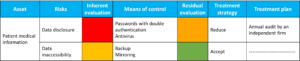
There are two main risks associated with this asset: data disclosure and data inaccessibility. For each risk, you will need to define, for example, in a matrix :
- The gross assessment
- Means of control
- Net valuation
- Treatment strategy
- Any treatment plans in place
7/ Information security objectives
ISO 27001 requires the setting of objectives and performance indicators linked to information security. For these objectives to be meaningful, they must be quantified. Here are a few examples:
- 100% data accessibility
- 0 data disclosures over the year
- -50% fewer information security incidents
- Restore customer data backups in less than 2 days
8/ Documented information management
A great deal of information will need to be documented when implementing your ISO 27001-certified ISMS. You’ll need to describe how the company’s activities are carried out, who does what in the company, and so on.
We recommend that you draw up a document, often referred to as the “Document Management Rules”. This document will formalize the rules to be followed for managing and describing this information. It contains information such as:
- Document types: forms, operating modes, procedures, videos, etc.
- Updating procedures
- Communication and distribution methods
- Validity periods
Drawing up “Document Management Rules” ensures that documentation is well described, regularly updated and understood by all.
9/ ISO 27001 control points
The ISO 27001 standard requires the implementation of control points or measures to ensure proper control of information security risks. There are 4 main families of measures:
- Operational
- Applicable to people
- Physical
- Technological
All these control points must be described in a document produced by the company. This is the “Declaration of Applicability”. Below are a few examples of concrete measures to be implemented for each family.
9.1/ Organizational measures
Return of assets :
– Procedure for returning information assets
– Access controls to information assets Planning and preparation for information security incident management :
– Crisis management procedure
9.2/ Measures applicable to individuals
Selection of candidates :
– Criminal record and diploma checks
Confidentiality or non-disclosure agreements :
– Signature of NDAs with employees, service providers, etc.
9.3/ Physical measures
Securing offices, rooms and facilities:
– Badge access
– Surveillance cameras
Secure disposal or recycling of equipment :
– Procedure for handling obsolete equipment
9.4/ Technological measures
Secure authentication :
– Software access rights
– Passwords / Double authentication
– Password change policy
Protection against malicious programs :
– Installation of antivirus software
Backup of information :
– Data backup
– Backup restore checks and tests
10/ Communication and awareness
This involves training and informing employees, as they are the ones who will implement the ISMS and ensure its success. You can do this by sending out monthly newsletters, organizing information sessions, running quizzes or phishing tests. During these events, it will be important to communicate on the following topics:
- Project progress
- Information security policy
- Documentation management
- Participation in continuous improvement (how to report incidents and improvements)
- Internal audits
- ISO 27001 certification audit

11/ Handling non-conformities
One of the objectives of an information security approach is to collect non-conformities to ensure that problems that have already occurred do not recur.
To meet this requirement, you’ll need to describe a procedure that explains how to deal with non-conformities. The same applies to improvements.
These procedures will be a great help to business staff, who are not always trained in information security: it will encourage them to report problems and be proactive.
12/ Skills assessment
As with most ISO certifications, it is essential to assess the skills of employees and identify their knowledge. This will help ensure that processes are carried out correctly.
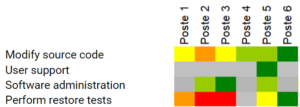
Using a matrix like the one below, you can easily distinguish the skills of each employee and identify any gaps.
If skills are lacking, you’ll need to train the staff concerned, coach them, recruit or outsource. This information needs to be tracked and documented.
13/ ISO 27001 internal audits
Internal audits are used to check everything that has been put in place to achieve ISO 27001 certification.
As part of this process, employees will need to be trained in internal auditing. They must draw up an audit plan to identify the positions, activities and roles to be audited. The auditors will then conduct interviews with employees to check that activities are running smoothly. They will be able to gather suggestions for improvement or incidents that may have occurred.
The results of these internal audits should be passed on to management for appropriate action. It is important to keep these audit reports, as they will serve as evidence during the internal certification audit.
14/ Management review
At least once a year, management should organize a review of the ISMS to ensure that it is still adapted, appropriate and effective. During these meetings, it will be important to address the following topics:
- Progress on actions decided at previous reviews
- Information on information security performance: non-conformities and improvements, indicators, internal audits, resources allocated to the ISMS, objectives, etc.
- Effectiveness of actions taken in relation to risks and opportunities
- Areas for improvement
15/ Improvement management
During the previous stages, improvements were identified. Now it’s time to formalize them and implement appropriate actions. Beforehand, you can create a procedure and a system for managing improvements.
16/ ISO 27001 certification audit
After all this work, the project finally comes to fruition: ISO 27001 certification. With ISO 27001 software such as Optimiso Suite, the auditor will have access to all the elements of your ISMS in just a few clicks. For example, he or she will be able to see a process map, dashboards for monitoring controls, asset inventories, or even what has been put in place for each of the standard’s requirements.
The ISO 27001 certification audit takes place in 2 main phases, also known as stages.
Stage 1: This phase can also be called the “pre-certification audit”. The auditor meets with the ISMS project manager and management to ensure that all documentation is present, and then gives the go-ahead for
Stage 2: After this first stage, you will receive the audit plan. Stage 2: This is the actual certification audit. In accordance with the audit plan, the auditor will meet with the ISMS manager, management and a number of employees to verify the following elements:
- Management commitment
- Compliance with ISO 27001 requirements
- Continuous improvement
- Implementation of a risk-based approach
- Employee involvement in the ISMS
After the audit, the auditor will communicate his position on the certification decision and share any discrepancies identified. He will then recommend your company to the certification body. A few weeks later, you will receive the audit report and your certificate.
After certification
Congratulations, you are now ISO 27001 certified! This marks the start of a new adventure in keeping your Information Security Management System up to date and improving it. You’ll need to :
- Monitor certification with the certification body
- Manage documentation and ensure that it is accessible and up to date
- Reassess risks and opportunities
- Monitor information security indicators
- Conduct internal audits
- Reassess skills
- Reassess suppliers
- Monitor non-conformities
- Manage improvements
- Communicate your ISMS procedures internally and externally
- Organize a management review at least once a year
ISO 27001 certification is organized in 3-year cycles. After the certification audit, surveillance audits will take place every year (years 1 and 2), followed by a renewal audit every 3 years.
In conclusion, these 16 steps structure the implementation of an information security management system and the achievement of ISO 27001 certification. They should enable you to reap all the benefits of an ISMS that is useful to both employees and management.
Summary
What is ISO 27001 certification?
ISO 27001 certification is an international recognition that enables companies to implement an Information Security Management System (ISMS).
It proves that the company has established control measures to secure sensitive data and ensure their confidentiality, integrity, and availability.
By obtaining this certification, a company demonstrates its commitment to information security and strengthens the trust of its clients and partners. With the rise of cyber risks in recent years, this certification is required in many fields.
What are the 4 security principles according to ISO 27001 standard?
The 4 security principles according to ISO 27001 standard are:
- Confidentiality: ensuring that information is accessible only to those authorized.
- Integrity: ensuring that data is accurate, complete, and protected against unauthorized alteration.
- Availability: ensuring that information is accessible to authorized users when needed.
- Authenticity: ensuring that users are who they claim to be and that the data is reliable and unaltered.
Why obtain ISO 27001 certification?
Obtaining ISO 27001 certification offers several benefits:
- Data protection: Ensuring the security and confidentiality of the company’s and its clients’ sensitive data.
- Risk reduction: Efficiently identifying and managing information security risks, thus preventing incidents.
- Trust building: Establishing trust among clients, partners, and stakeholders by demonstrating the company’s commitment to information security.
- Reputation improvement: Enhancing the company’s reputation as a reliable and responsible entity in terms of information security.
- Process optimization: Implementing effective procedures for managing information security, which can lead to an overall improvement in the management of the company’s activities.
How long does it take to obtain ISO 27001 certification?
The time required to obtain ISO 27001 certification depends on several factors. This includes the size of the company, its level of preparedness and compliance, as well as the complexity of its processes.
On average, it can take several months to a year or more.
Good project management, full involvement of employees and management are essential to ensure the success of the certification process.
What is the duration of an ISO 27001 certification cycle?
Once obtained, ISO 27001 certification is valid for 3 years. Each year, a surveillance audit will be organized to ensure that the company maintains compliance with ISO 27001 standards.
